Intrusion Detection Brings Peace of Mind
IDS-2200 was created to fulfill a need for real-time, on-line security monitoring and reporting within the OS 2200 operating environment.
IDS provides tools for security analysts and administrators to be aware of security-related events on the OS 2200 systems they administer. This may include unauthorized attempts to access data and system resources.
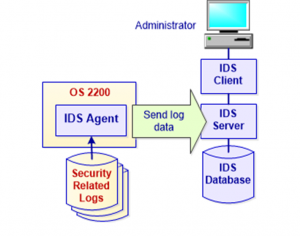
The IDS OS 2200 Security Agent runs in background, on OS 2200 host systems, monitoring system logs and other sources for security related events. The IDS Security Agent transmits the event data to the IDS Server, on a Windows-based platform. The IDS Server receives and analyzes data for these events as they occur. It stores the data in the IDS Database for future access. Authorized administrators use IDS client programs to access reports and security data on the IDS Server, and to configure the product.
Convenient User Features
Release Announcements
Product Description
Learn how IDS helps you monitor security on your OS 2200 platform.
IDS is compatible with Unisys’ OS 2200 security philosophy and implementation.
Intrusion Detection fulfills what is often a critical missing component in a site’s overall security tool set.
IDS in one simple view
The premise of IDS-2200 is to monitor security-related events on your 2200 system via key log data. An IDS Agent, installed on your 2200 partition, gathers data from several security-related log files. It passes this data to an IDS Server which stores the data in a database. Administrators and authorized users log into IDS Client programs to configure the product and to use it in operational settings.
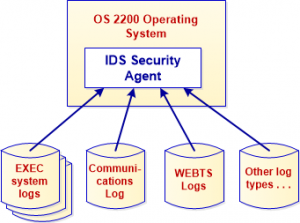
Gathering all the data you need to help you monitor users’ access of your OS 2200 resources.
What are these security related logs?
Most importantly, the IDS Security Agent gathers data from the EXEC system logs. It pulls records of when users sign on to the system, when they assign a file or tape, etc. OS 2200 has numerous components. IDS also gathers log data from several kinds of communications logs. Also contributing to the data are WEBTS logs, and other minor log types.